Single Sign-On
Deepfence Cloud supports single sign-on using Google, GitHub and Microsoft by default. Additionally, you can configure any OpenID Connect ID provider like Okta.
Okta - OpenID Connect
To configure Okta as ID provider for Deepfence Cloud, please follow these steps
-
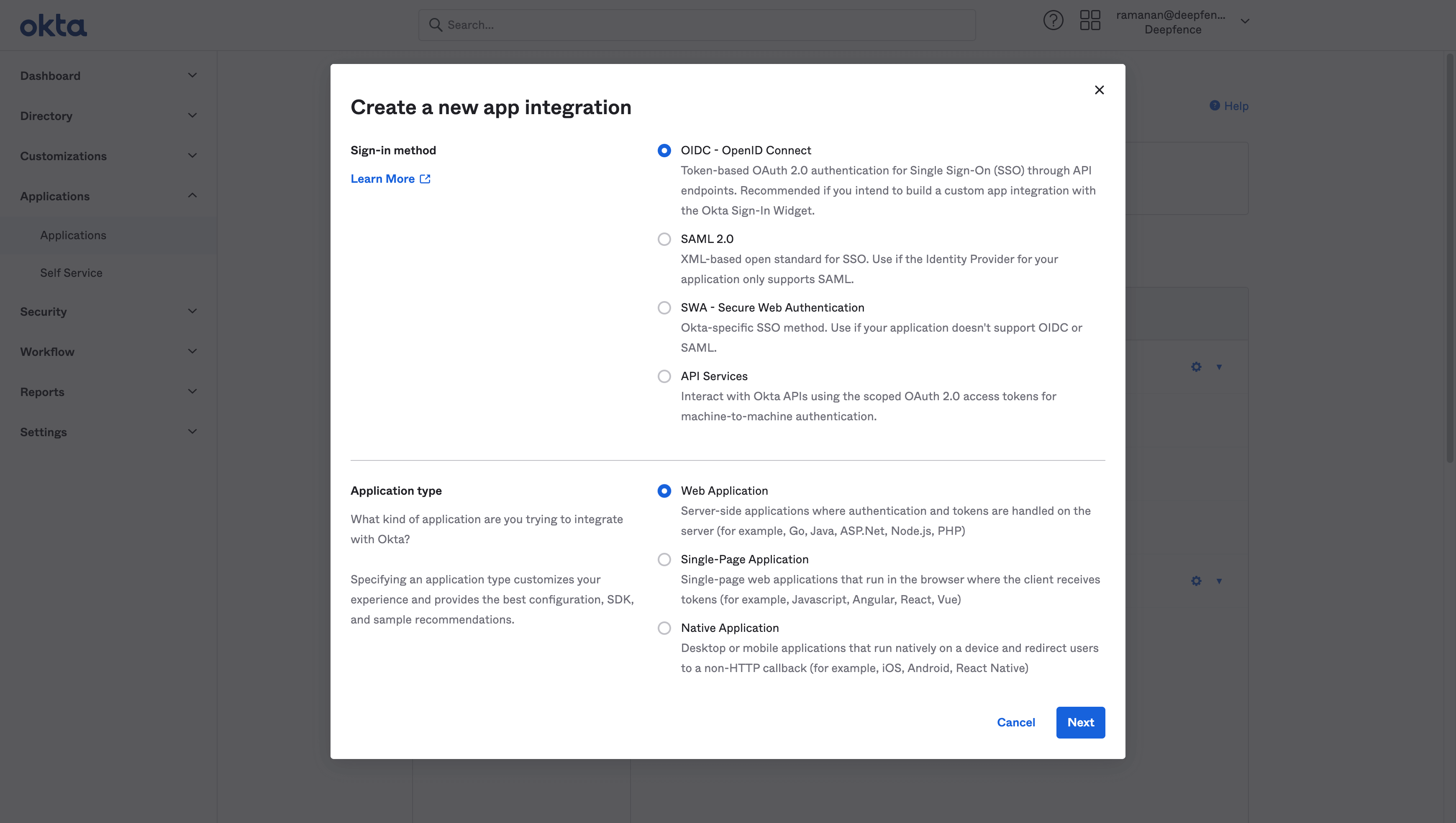
Create new app integration in Okta's admin console
-
Choose
OIDC - OpenID ConnectandWeb Application -
Select
Refresh TokenandImplicit (hybrid) -
Set
Sign-in redirect URIstohttps://deepfence.cloud/deepfence/auth/callback/oidc -
Set
Sign-out redirect URIstohttps://deepfence.cloud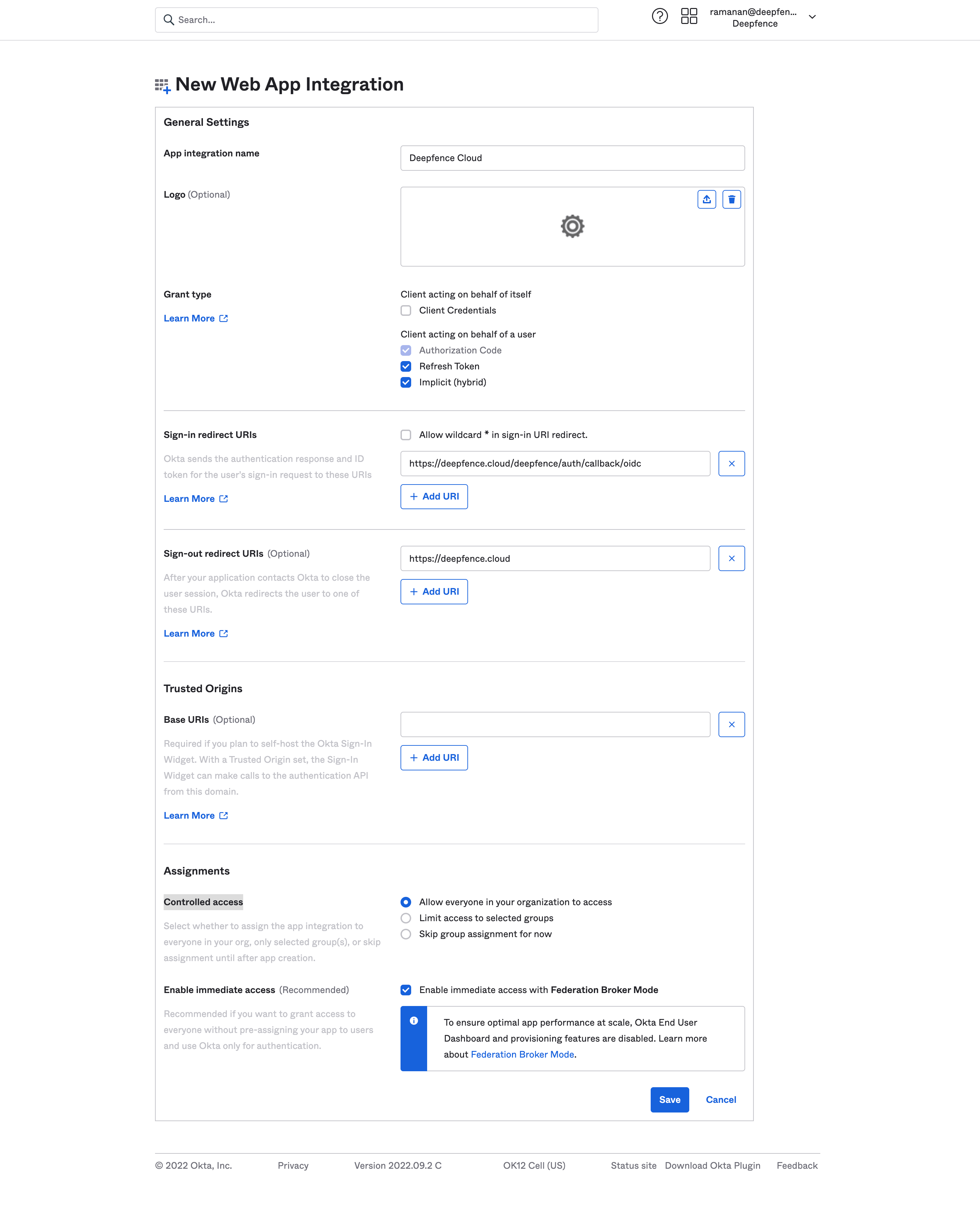
-
You can configure
Controlled accessas per the requirements -
Click
Save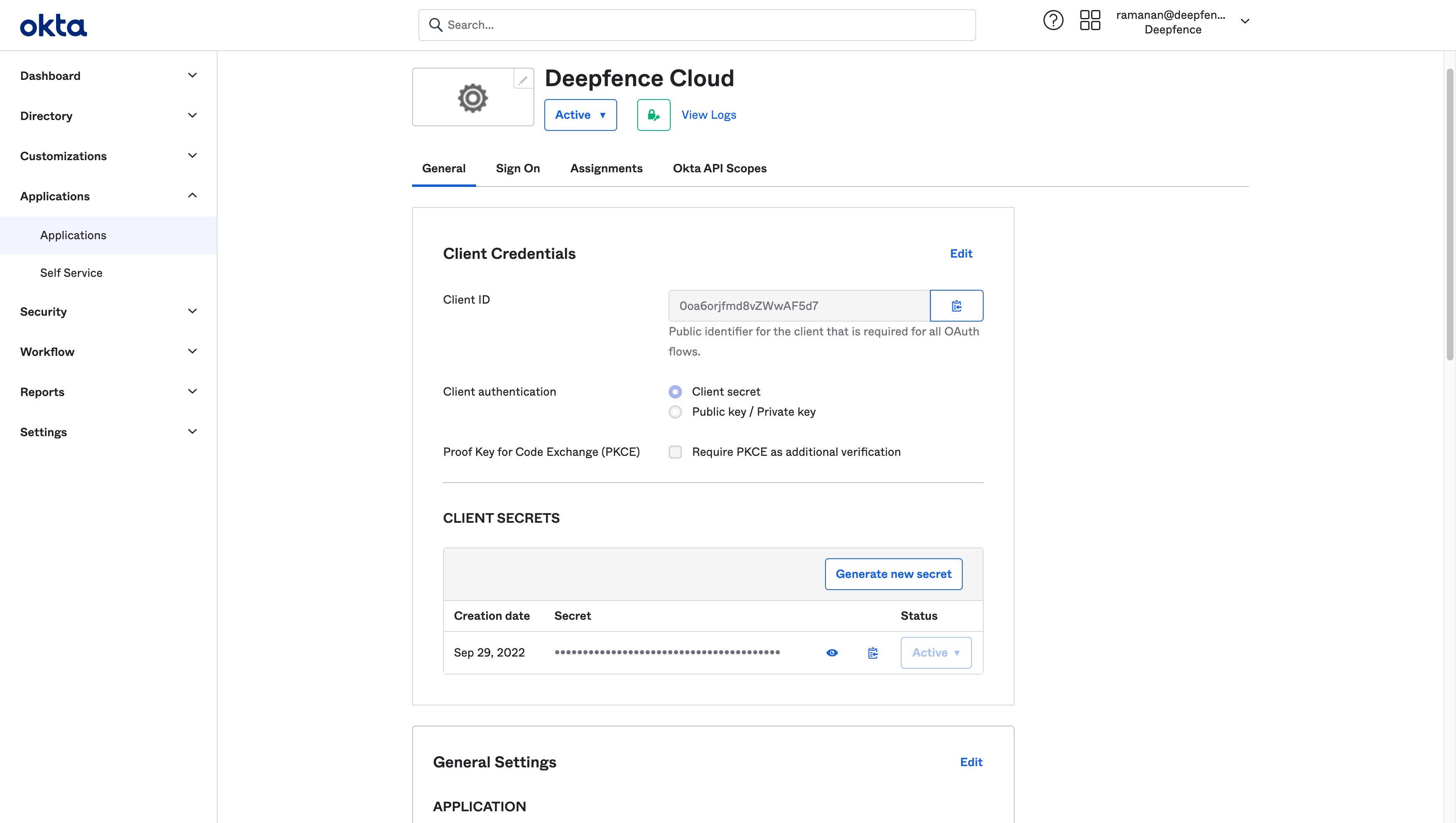
-
Copy the
Client IDandClient Secret.
Configure OpenID Connect in Deepfence Cloud
-
Register to Deepfence Cloud using username and password or social login.
-
Click user profile menu on the top right and then click
Organization Settingsand thenSSO Configurationtab.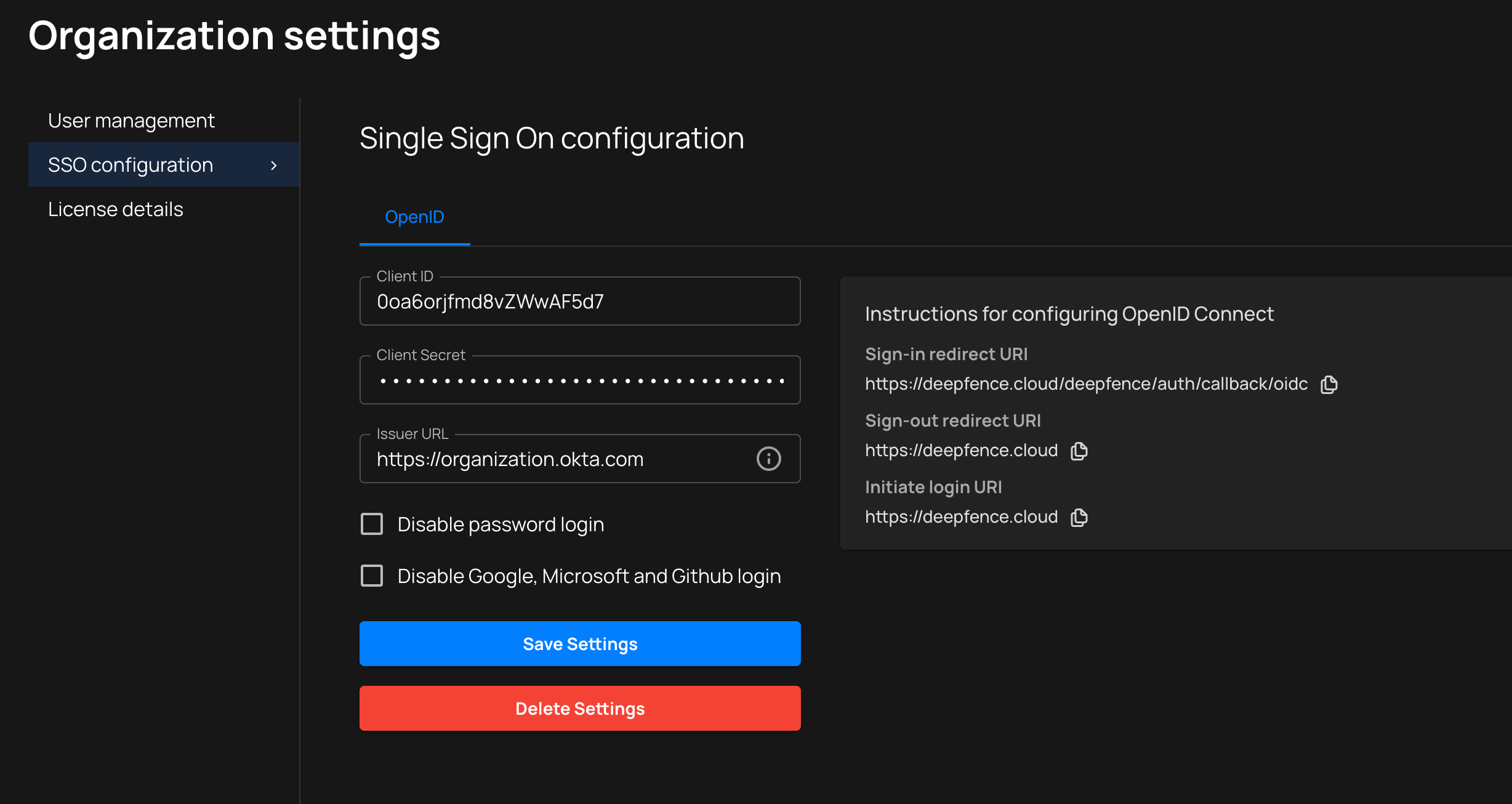
-
Enter the
Client IDandCliet Secretfrom the OpenID Connect provider, in this example, from Okta. -
Issuer URLis the ID provider's URL. Example:https://organization.okta.com -
Optionally you can disable password login and social login (Google, GitHub, Microsoft).
When password login is disabled, users invited to the platform will continue to provide a password during registration. However, OpenID Connect will be used for authentication.
-
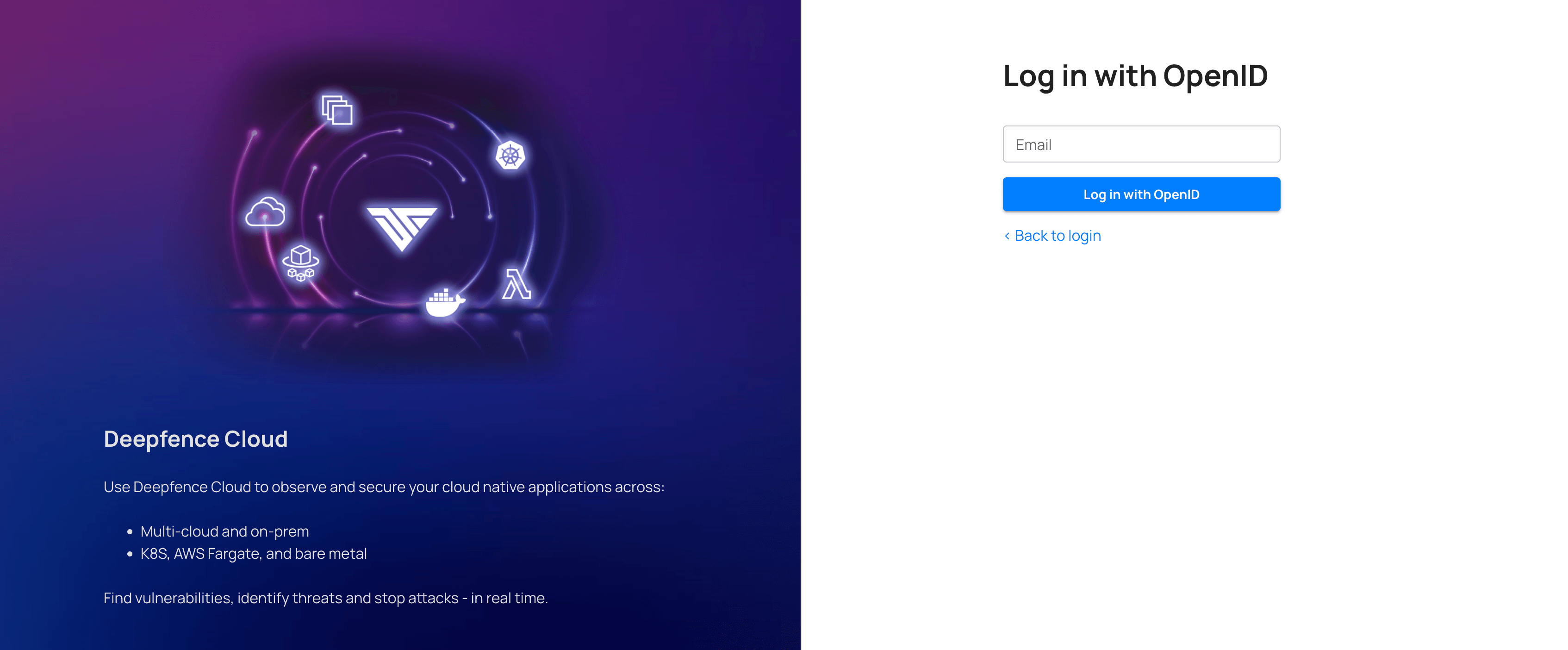
On the login page, click
Login with OpenIDand enter your email id to log in with the configured SSO.