AWS ECR
You can add your private and public ECR repositories to ThreatStryker to scan for vulnerabilities, secrets and malwares.
Adding ECR repository
-
Select
ECRregistry type from the registries section.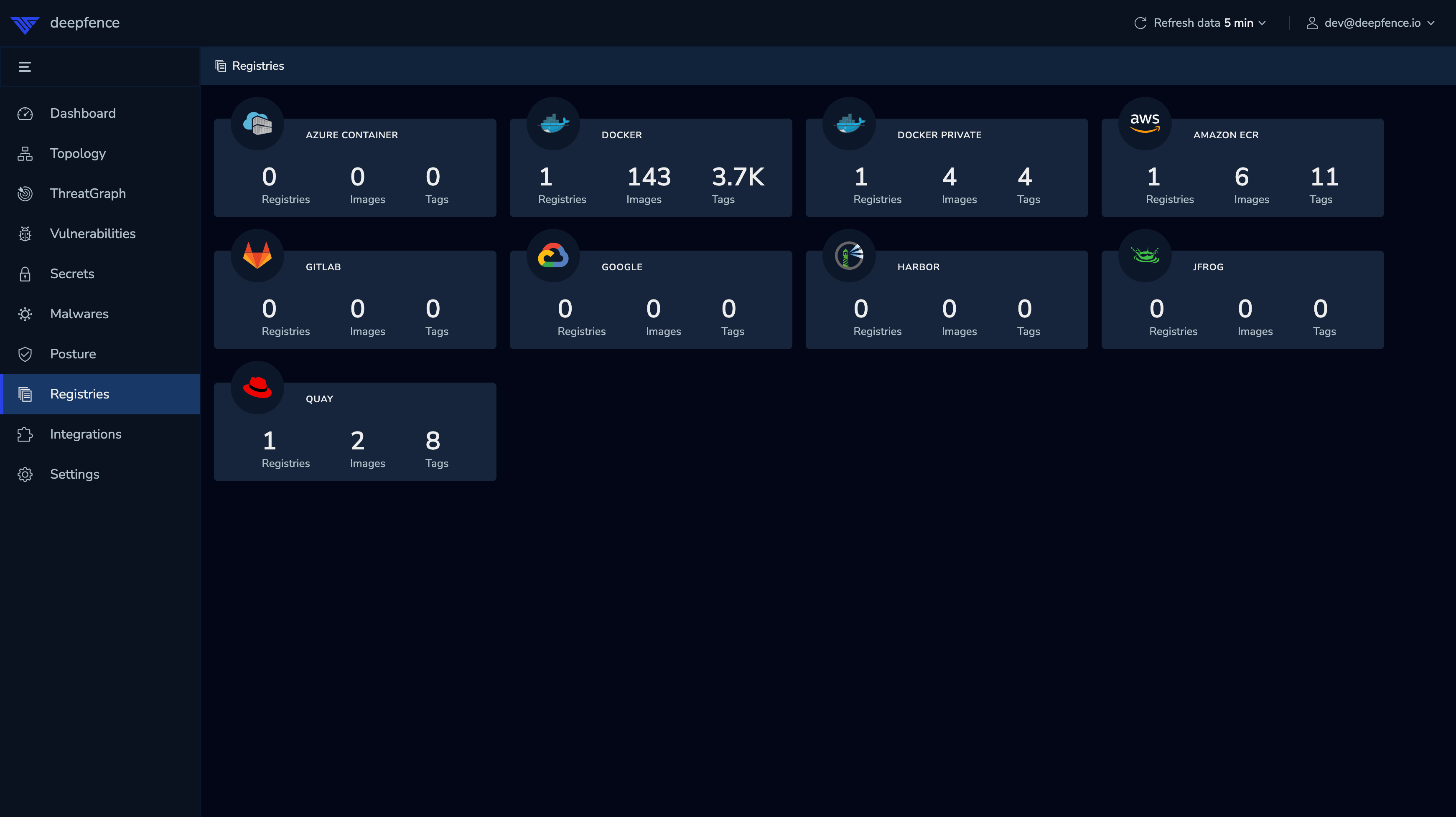
-
Click on Add Registry button to get the following form:
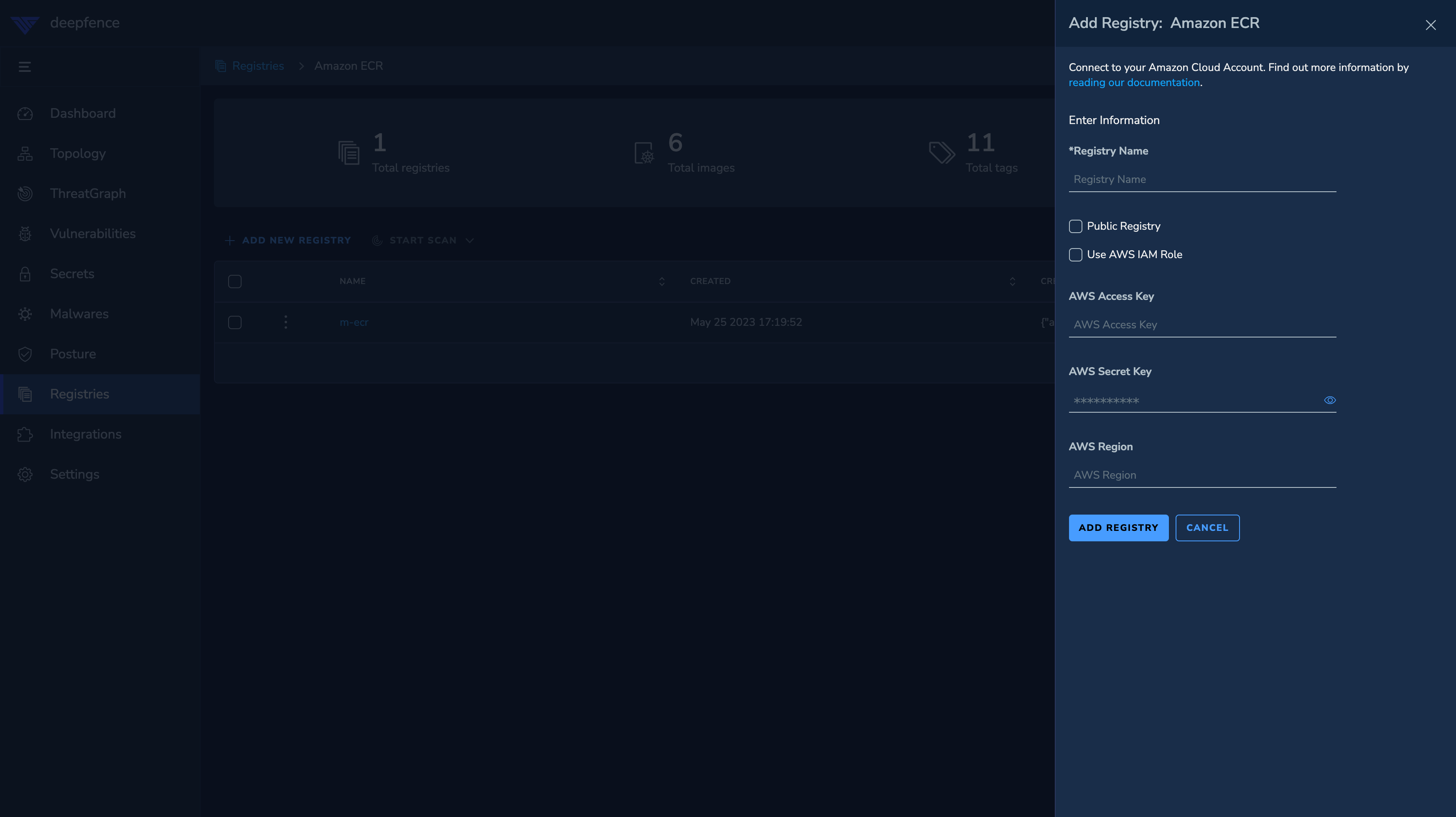
-
Enter
Registry Namefor reference later. Then, enter the other details as per the deployment.
Using Credentials
-
Fill in the credentials(
AWS Access Key,AWS Secret Key) for the user with access to the ECR registry. -
For private registry, fill in the
AWS Regionwhere the registry is located. Else, for public registry, togglePublic Registry.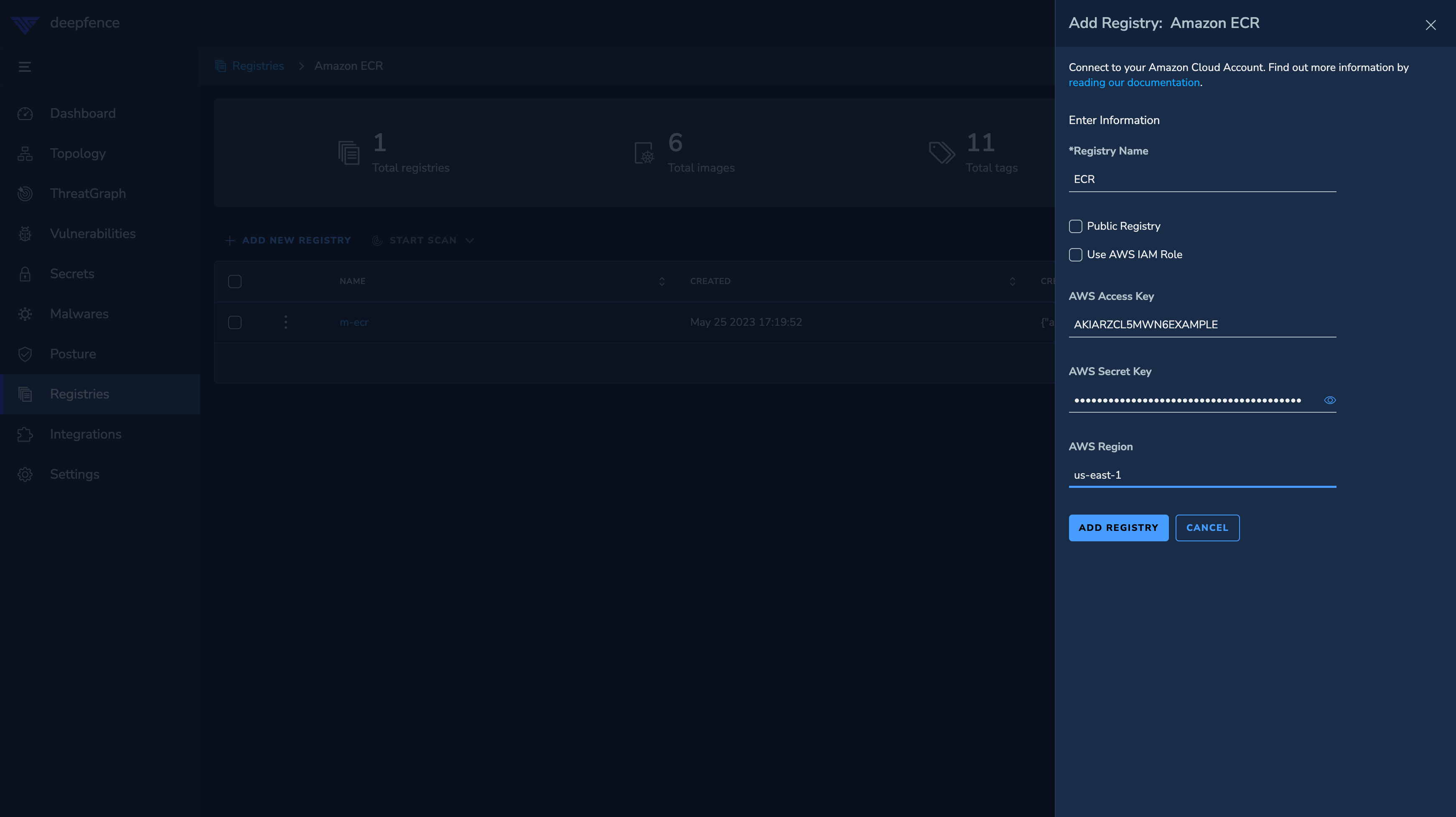
Using AWS IAM Role
The Deepfence Console needs to be deployed on AWS EC2 instance in the same AWS account as the ECR registry and the EC2 instance needs to be assigned an IAM role with the correct permissions
-
The IAM role to be assigned to the Deepfence Console EC2 instance can be deployed using CloudFormation with deepfence-ecr-role-setup.template.
-
Link to create IAM role. Change region, if required. Once completed, go to
Outputstab and copy the value ofInstanceProfileARN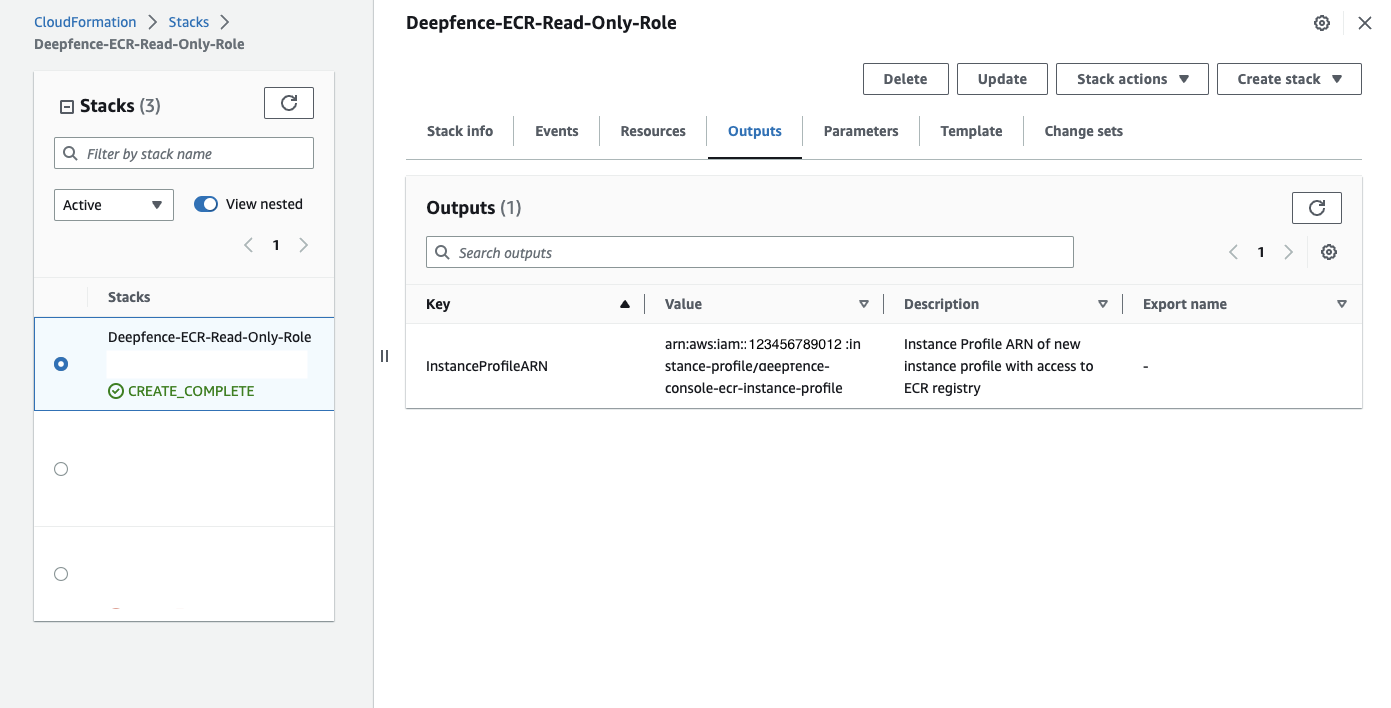
-
Assign the instance profile to the EC2 instance on which the Deepfence Console is hosted.
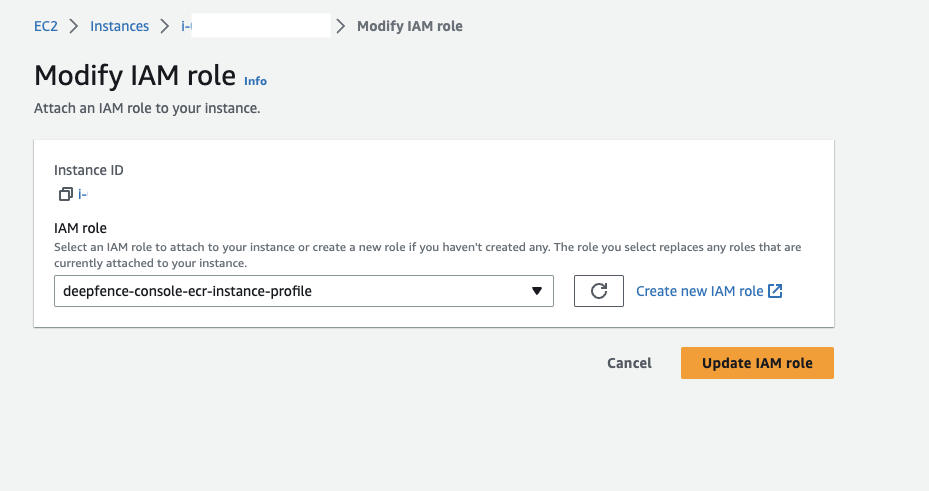
-
-
For private registry, fill in the
AWS Regionwhere the registry is located. Else, for public registry, togglePublic Registry. -
Leave the
AWS Account IDandTarget Account Role ARNfields blank as they are only used for the cross-account scenario below.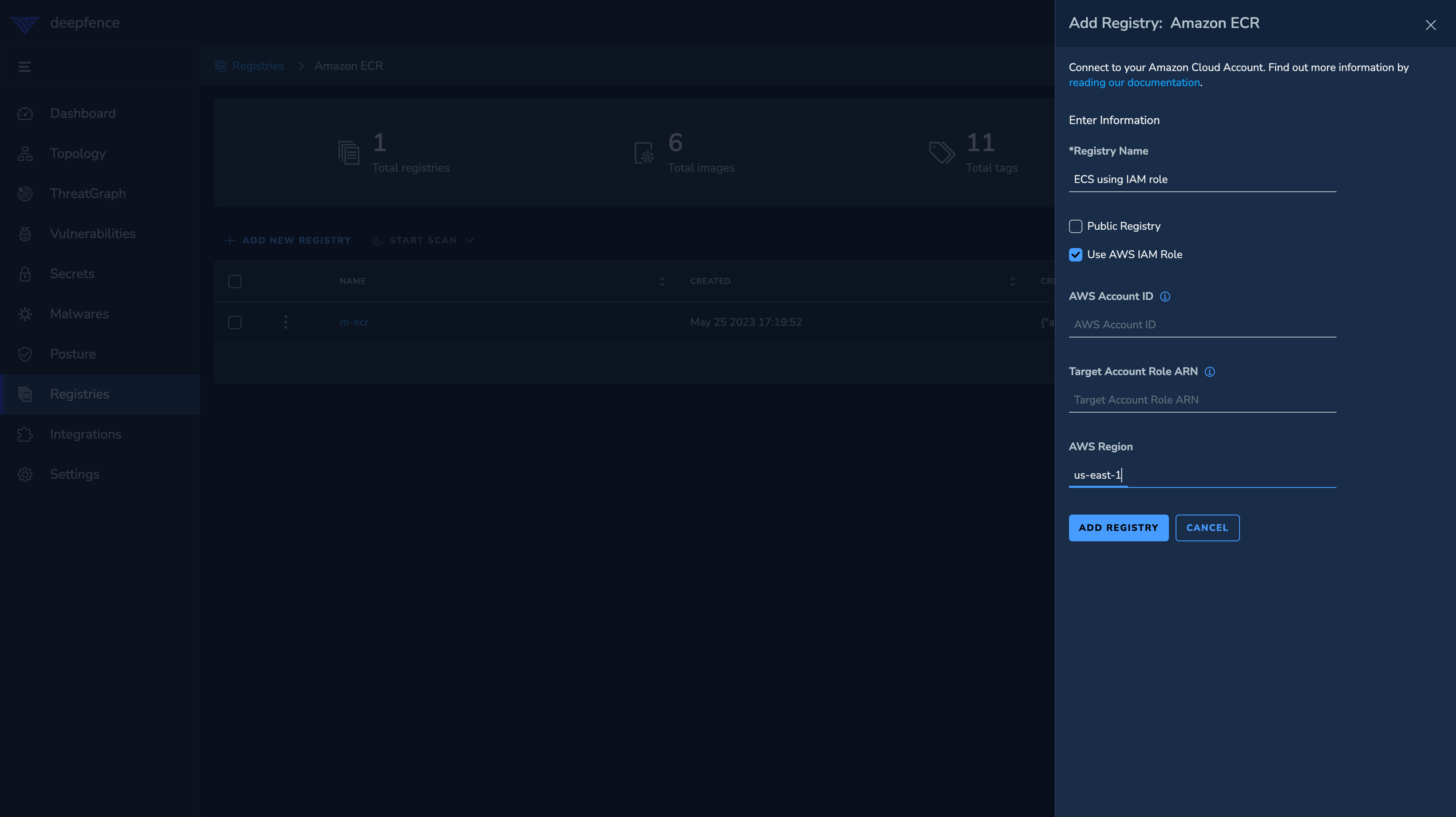
Using AWS IAM Role (with Cross-Account ECR Registry)
If a user has an ECR registry in one AWS account and Deepfence Console is deployed in another AWS account, the user needs to set up cross-account ECR registry access as per the following steps:
-
Create a role in the target ECR registry account which has required pull permissions. This can be deployed using CloudFormation with deepfence-cross-acc-ecr-role-setup.template
-
Link to create role. Change region, if required. Once completed, go to
Outputstab and copy the value ofRoleARN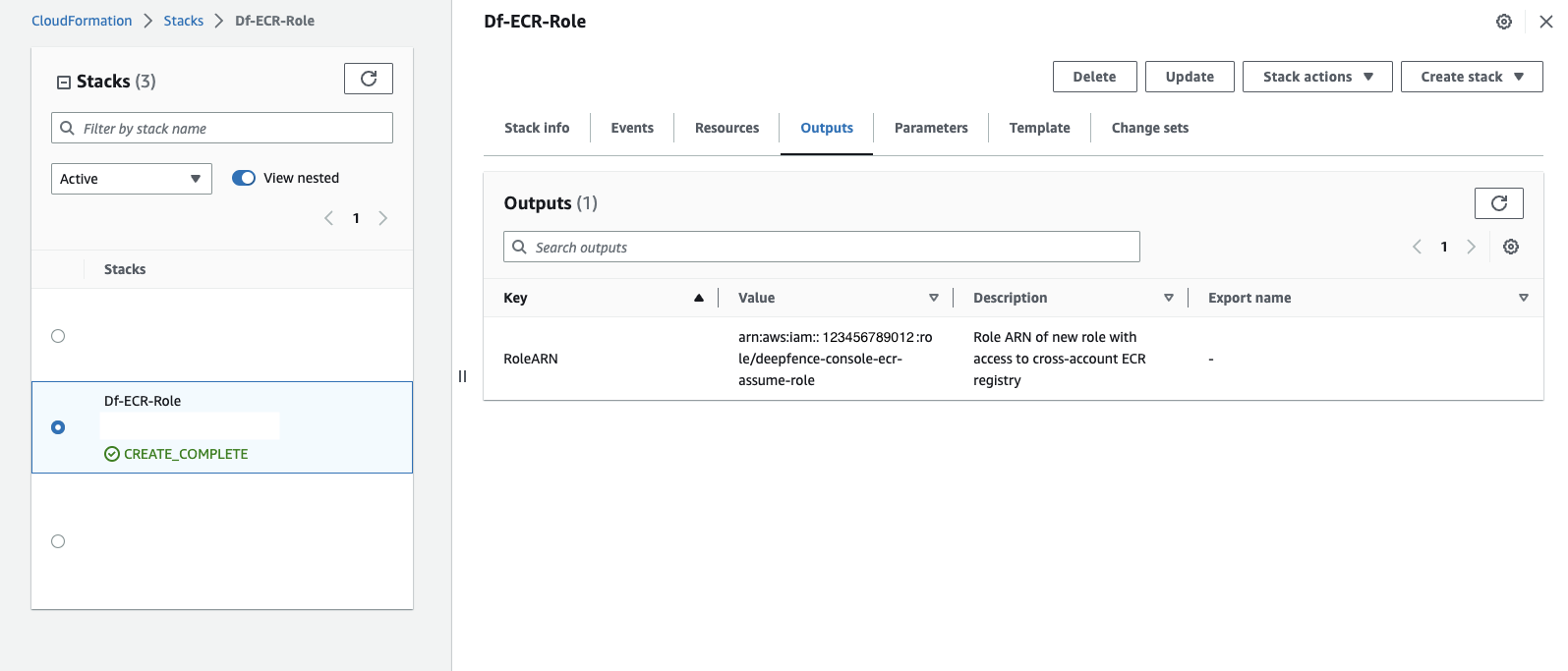
-
-
Create a role in the account where Deepfence Console is deployed to assume the role created in the step above. This can be achieved using CloudFormation with deepfence-console-account-setup.template.
-
Link to create cross-account instance role. Paste the
RoleARNcopied from above step intoECRAccessRolebox.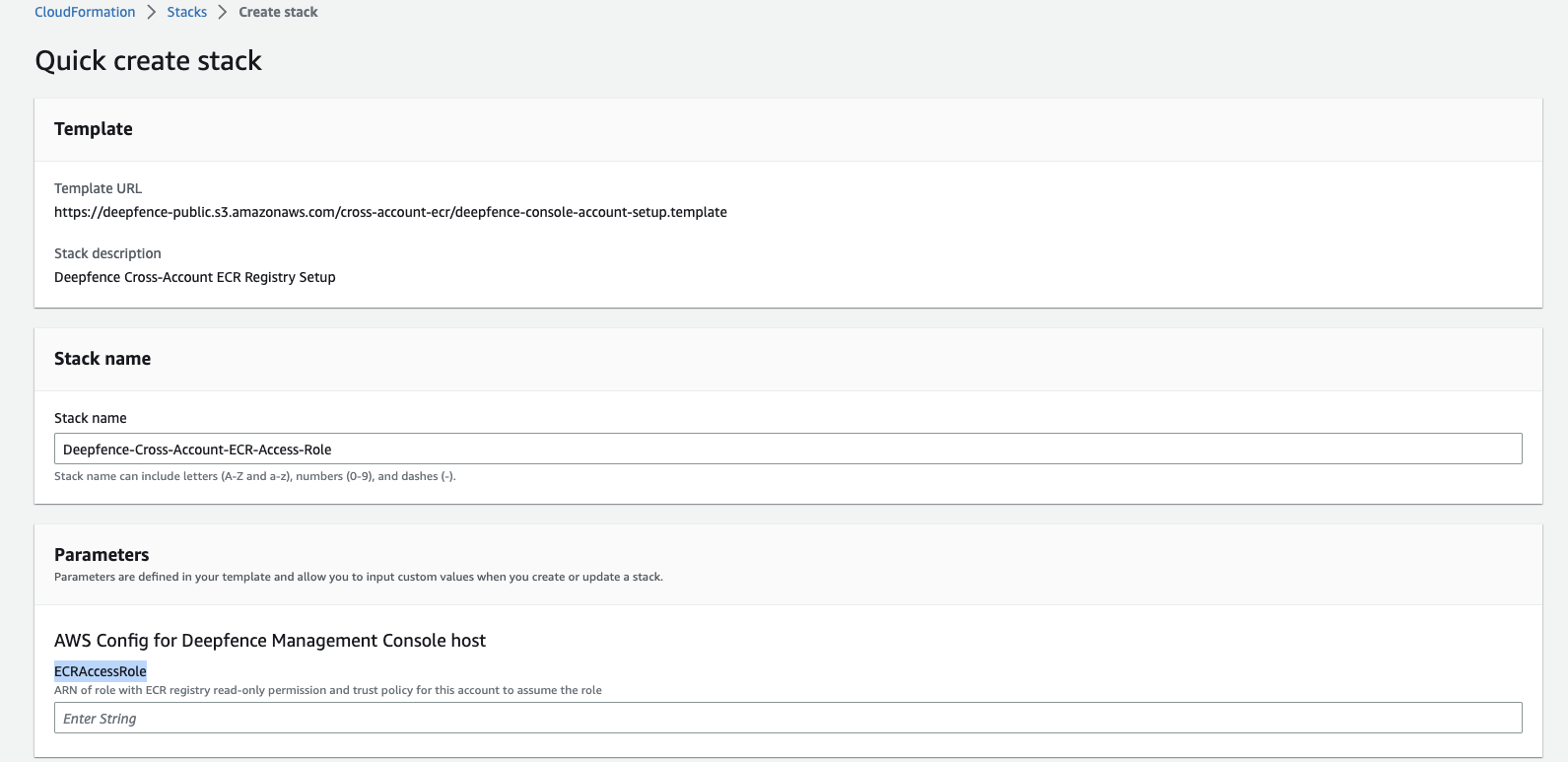
-
Once completed, go to
Outputstab and copy the value ofInstanceProfileARN.
-
-
Assign the instance profile role ARN created above to the Deepfence Console EC2 instance.

-
For private registry, fill in the
AWS Regionwhere the registry is located. Else, for public registry, togglePublic Registry. -
Fill the account id of the target account where registry is located in the
AWS Account IDfield. In theTarget Account Role ARNfield, paste the value of theRoleARNfrom the above steps.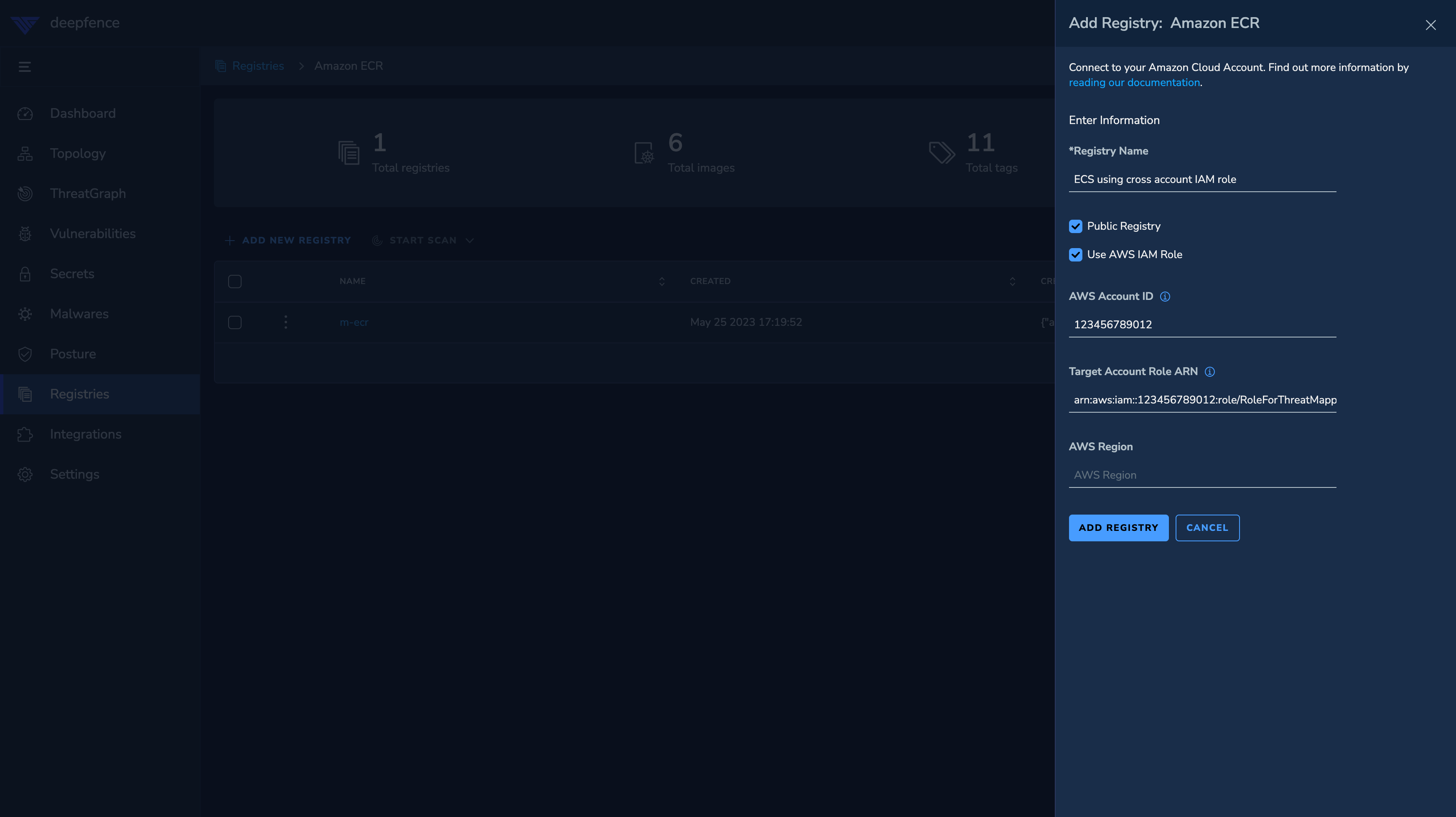
Adding ECR repository - Kubernetes
If Deepfence console is deployed in EKS, please follow these steps to configure IAM role which will be assigned to Kubernetes service account.
Pre-requisite:
-
Associate OIDC provider with the EKS cluster where Deepfence management console is going to be deployed.
(refer here for aws documentation on enable-iam-roles-for-service-accounts)
-
kubectl and helm command line tools are installed and configured to access the cluster where Deepfence management console is going to be deployed
- Create the EKS IRSA role using the cloudformation template deepfence-ecr-registry-role-for-eks
- Note namespace, service account name and iam role arn from the output of terraform or cloudformation deployment
- Follow the instructions here to download the
values.yamlfrom Console helm chart for customization. - Edit the
values.yamland set the ServiceAccountserviceAccount:
# Specifies whether a service account should be created
create: true
# Annotations to add to the service account
annotations:
"eks.amazonaws.com/role-arn": "arn:aws:iam::123456789012:role/deepfence-ecr-role"
# Service account name
name: "deepfence-console" - For ECR configuration, please refer the instructions above